If you look at the CBC diagram, you'll see that having a fixed IV is equivalent to having the first ciphertext block become the IV. If your cipher is a good pseudorandom permutation, then what you are doing does work, if and only if all timestamps are unique such that the "new IV" is unique and unpredictable.
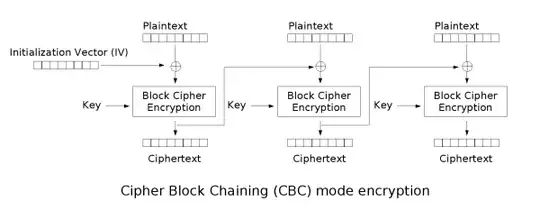
And in fact, if you do not use the decrypted value of the first block (the "IV") this is provably just as secure as normal CBC in the ideal cipher model, as the IV requirements of CBC (uniqueness and unpredictability) happen to coincide with what a pseudorandom permutation does.
If you do use that value, I am not sure. I believe it is still secure but cannot think of a convincing argument of why it is (or is not) right now, perhaps someone can complete this.
You may also set the "fixed IV" to zero for convenience - its value is irrelevant.
That said, it is probably best to fix your IV transmission, just to do things cleanly and not have to explain your weird IV trick. After all, if you can transmit the ciphertext, why can't the IV make it?
