When sending a block to be decrypted or encrypted, with RijndaelCBC, we input the data to decrypt/encrypt and an IV for syncing and to prevent identical outputs for identical inputs.
This question is regarding to any loopback mode use of AES chipher block using an IV, but my experience is with CBC.
Inside the RijndaelCBC "machine", (model), the input IV is processed and changed through a number of XORS with an end result (logically) different from the input IV.
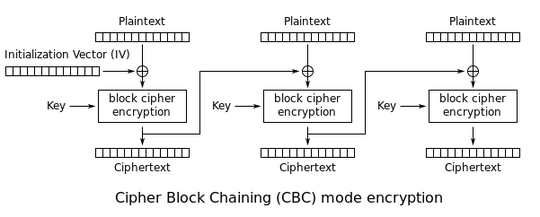
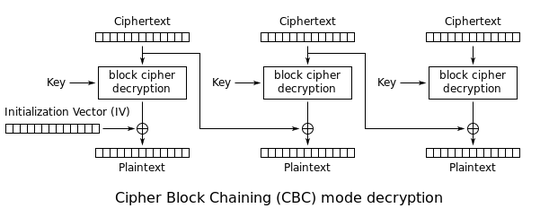
Because of the symmetric nature of RijndaelCBC the encryption process and decryption process will both change the input IV to a different valued buffer then the original but an identical result for both processes.
My questions are:
- Does this "Output IV" holds information that can have private key or plain data value inferred from?
- Is using the IV in such a way, which can keep both sides of a Rijndael secured communication link sync data (IV) up to date without the need of sending the IV over communication (Although it is not secret), is a known and used approach?
Example for the second question:
Variables: PrivateKey, StartIV
Box A and Box B are connected on a Rijndael secured link.
User Ainputs and receives data from Box A, while User B inputs and receives data from Box B.
User A → Plain Data → Box A →
Enc(Plain Data,PrivateKey,StartIV) →
OutputIV, EncedData → SecuredLink
User A sends plain data to box A, it is then encrypted using a starting IV and private key, saving the output IV from the encryption operation, while sending the encrypted data to Box B through the secured link.
SecuredLink → EncedData → Box B →
Dec(EncedData, PrivateKey, StartIV) →
OutputIV, Plain Data → B User
Encrypted data received from the secured link in Box B which then decrypts the encrypted data, using the private key and start IV, to plain data; saves the output IV and sends the plain data to the user.
User B → Plain Data → Box B →
Enc(Plain Data, PrivateKey, OutputIV) →
NextOutputIV, EncedData → SecuredLink
User B sends plain data to box B, it is then encrypted using the OutputIV, (Generated output from decrypting the message arrived from Box A), and private key, saving the output IV from the encryption operation as the next output IV, while sending the encrypted data to Box A through the secured link.
SecuredLink → EncedData → Box A →
Dec(EncedData, PrivateKey, OutputIV) →
NextOutputIV, Plain Data → User A
Encrypted data received from the secured link in Box A which then decrypts the encrypted data, using the private key and the OutputIV, (Generated output from encrypting the message that was sent to Box B), to plain data; saves the output IV as the next output IV, and sends the plain data to the user.
Now i might be very naive but i don't understand why not to use this approach and save the syncing operation over communication.