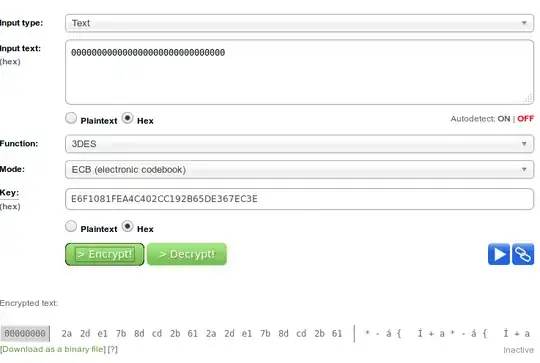
I am trying to verify a Triple DES Key Component generated by PC Crypto. The key portion is:
E6F1081FEA4C402CC192B65DE367EC3E
and the KCV value that should be returned is:
212CF915
In theory, it should be calculated as: encryption of binary 0's with the key portion with 3DES.
I have been trying the following link, but the calculation doesn't work. http://tripledes.online-domain-tools.com/
I used the following parametrization on the online tool.
Could anyone confirm that the calculation is performed as I mentioned?