AES has been studied for many years by experts in the field, and the estimates on how long it would take to break are based on the best known public cryptanalysis. Your algorithm has likely not received any expert study, so any estimates would be meaningless.
Instead of trying to estimate how good the cipher is you could try to understand how the BNN works, what it does to the bits, whether it achieves good mixing, confusion and diffusion, and whether you can find an attack.
Also take note of Schneier's "law": "Any person can invent a security system so clever that he or she can't imagine a way of breaking it".
If you don't find an attack, that doesn't mean it's secure.
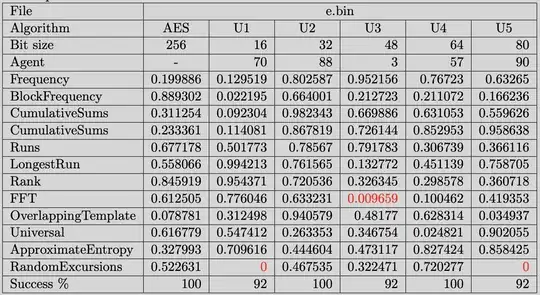
Please also note, that the statistical randomness tests you perform can give you with some level of confidence an answer that something is broken, but they most definitely cannot tell you that something is secure. The problem with these tests is that they presume an adversary model - that is they take one specific adversary and state that the scheme is secure against this adversary. However, that does not rule out the existence of another adversary that breaks it. Additionally, these tests are statistical, so they will have the same flaws as any other empiric test.
In trying to find an attack you could also look at what other people have done in symmetric cryptography - the obvious ones would be methods like linear and differential cryptanalysis. But you could also look at what other's have looked into regarding neural networks for cryptography. One example here would be: https://arxiv.org/abs/1610.06918 .
I hope I could give you some pointers on what you could do next.
P.S.: Why is there a 1007% success chance at the bottom of the U2 column?