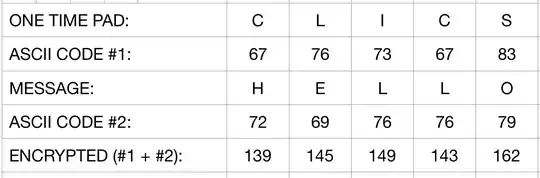
No, this is not a proper way to perform the One Time Pad, even with just 5 letters (assuming the pad and message are bound to be letters that is in range [65..90]).
Problem is, when we see that the first encrypted character is 139, and since we know that the pad is in range [65..90], we know that the first plaintext character is in range [65..74], not in range [75..90]. That's a huge information leak. When the ciphertext character is 130 (resp. 180), we exactly know the plaintext letter: it is 65/A (resp. 90/Z).
The solution to this problem is to compute ciphertext as $c=((p+m)\bmod 26)+65$, and decipher as $m=((c-p)\bmod 26)+65$ (implementable as (c-p+26)%26 + 65 in C). As a bonus, the ciphertext consists of letters.
My idea is to use the same Ascii #2 to again if the message is longer
That's a tried, tested, and bad idea. This is no longer a One Time Pad and it is no longer unconditionally secure. See for example How to attack the Two Time Pad?.