The chip user doesn't really do any PUFy stuff. PUF manipulation is not entirely deterministic, so the stochastic methods used to convert that to determinism are hidden within the bowels the ChipDNA thing.
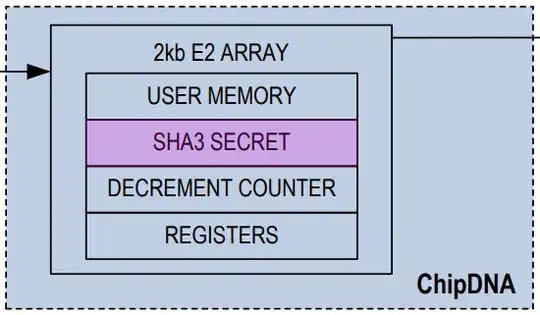
The security concept is that the PUF holds the SHA3 secret, which is simply a truly random (but fixed) bit sequence. The 'secret' can be an authentication key $(K)$ for use with the FIPS 198 keyed-hash message authentication mode (HMAC) functionality off the front page. Maxim have opted for SHA3 as the hash function. They suggest that SHA3 is better than the others?
Communications $(m)$ can be authenticated $ \operatorname{HMAC-SHA3}(K,m) $. But notice that there is no cipher component on the datasheet. The datasheet only deals with the electrical connectivity to the device. Note though that this chip only came out towards the end of last year. There mightn't be any cartridges that use it yet. Something simpler will be currently used. Security protocols and how the chip's components might be used exactly will be a trade secret for the particular printer manufacturer. We do know that "ChipDNA secure key never resides statically in registers or memory, nor does it ever leave the electrical boundary of the IC" as it's in Maxim's literature. But the chip's network ID is public, yet "The
unique ROM ID is used as a fundamental input parameter
for cryptographic operations and serves as an electronic
serial number within the application." There's an evaluation board for this chip, so you might have to buy one and experiment.
A use case for printers of the 3D type is:-
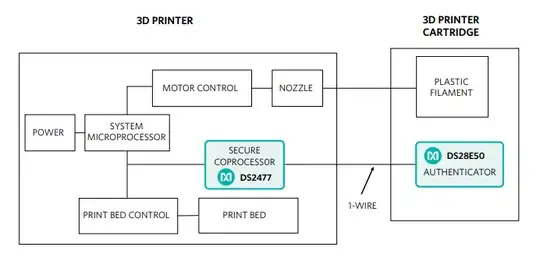
Sharing the other answer's distopian worldview, the chip also has a 17 bit down counter. This allows the cartridge to be forcibly scrapped after $2^x$ pages/metres of filament.

