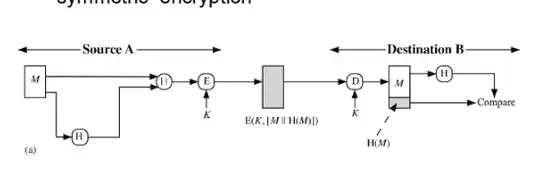
This structure provides message authentication. My question is if someone finds the key he can simply change the message and compute new hash according new message and send it to the receiver. If so, how can hashing provide message authentication? This scheme totally depends on encryption algorithm than why do we add hash in this?
1 Answers
As indicated by Dave in the comments, hash-then-encrypt may not provide authentication, so the scheme in the picture you provided may not be secure at all.
Let's assume for this answer that the encryption scheme used is such that hash-then-encrypt is secure. It could for instance be mapped to AES-GCM which uses GHASH, or Poly1305 correctly paired with a block cipher.
The idea of authenticated encryption is not to provide security against leaking information about the key. If the key gets known to the adversary then all protection is lost.
Authenticated encryption provides message integrity - protection against changes of the ciphertext. These changes may be deliberate, i.e. changes of the ciphertext during transport by an adversary or non-intentional such as data loss by lower levels in the transmission.
If you don't provide message integrity then an adversary may change the ciphertext and thereby alter the decrypted plaintext message without this being detected. It could also trigger the availability of a plaintext oracle that may even compromise confidentiality of the message. Note that hash-then-encrypt may not provide protection against padding oracles if CBC mode encryption is used, as the padding is (commonly) removed before the hash is verified.
Besides that, it provides message authenticity: proof that the plaintext as encrypted by an entity holding the secret key. Nobody else would be able to encrypt a valid hash after all.
In short, the hash is there to protect the message, it doesn't protect the key.
- 96,351
- 14
- 169
- 323