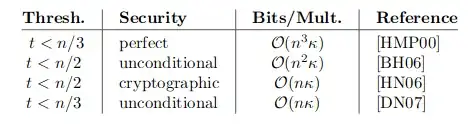
This paper refers to two distinct security models: perfect security and unconditional security. Until now, I knew of them as the same thing and equivalent to information-theoretic security.
From the paper, it's obvious that perfect security is the same as information-theoretic security. In this case, what exactly is unconditional security?