Is there a reason, why in pre-shared key mode, Wi-Fi session key is not secured with something like Diffie-Hellman but instead is derived from PSK key and some information exchanged in clear during sign-on?
6 Answers
As Thomas pointed out in his comment, in WPA-PSK the parties already have a shared secret (the pre-shared key), so there is no need to go through the step of Diffie-Hellman key-exchange -- unless you want perfect forward secrecy (PFS) (see update below).
In WPA, the client and the access point goes through a step known as the "4-way-handshake" to verify that the other party is in possession of the pre-shared key and to derive session keys for actual (encryption/authentication) usage. This step involves nonces from both sides, and some cryptographic computations, with the end result that 1) both parties can verify that the other party is in possession of the common secret and 2) they both have derived a shared session key which they will use for the actual encryption.
The picture below shows the steps in this process. The Supplicant is the client and the Authenticator is the access point. The PMK is the shared secret. In a typical home-user setup, the PMK is usually derived from a password using PBKDF (this password is what you normally punch in when connecting to a wireless network). The PTK is the derived key that they end up actually using for encryption.
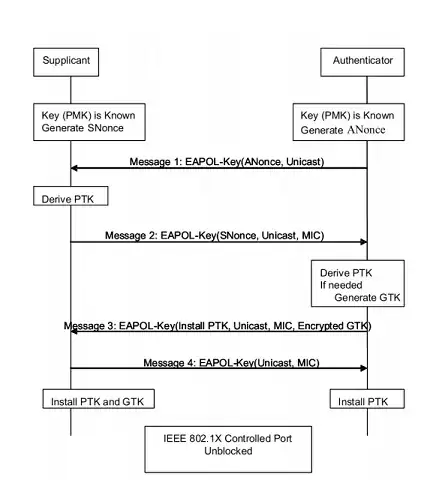
UPDATE
As mentioned in the comments, the above does not actually answer why WPA-PSK does not use DH. However, before discussing that, let's clarify what DH has to offer over what's currently being used, and also why the use of pre-shared keys diminishes some of those advantages. I claim that the one big advantage of using DH is that if offers perfect forward secrecy (PFS), while the ability to "separate" users from each other on the same WLAN is more debatable.
First we need to be clear about the kind of attacks we want -- and can -- be able to protect against.
Outsiders, i.e. attackers not knowing the PSK: If the PSK contains sufficient entropy (either drawn completely at random from a big key space or derived from a sufficiently long/complex password) and the PSK is kept safe and never leaked then DH does not offer anything over the current solution. If, however, the PSK is either lost or derived from a weak password, then the current system is completely broken. The reason is that the session keys are completely derived from the PSK, hence anyone who knows this can decrypt all traffic. Even worse, since it does not offer PFS, an attacker can go back an decrypt all previous traffic as well. The use of DH would prevent this. Since in practice most home WLANs uses a weak password to derive the PSK, DH would indeed be an upgrade.
Insiders, i.e. attackers knowing the PSK: Now consider the scenario where the attacker knows the PSK. What could the handshake offer then? As mentioned above, with the current system the answer is nothing. So what about DH? Assuming that in this scenario the PSK is only used to authenticate the DH exchange (say with a MAC), the DH would still offer security against a passive attacker, while nothing against an active attacker. Why? In the passive scenario, the attacker has to break the DH exchange which we assume is intractable. On the other hand, in the active scenario, the attacker can do a classic MitM attack, since he can forge valid handshake messages. Thus, under the typical conservative approach taken in formal security models, we would conclude that DH offers no security benefits over the current scheme since we always assume that the attacker is active. However, in practice, conducting an active MitM attack can sometimes be tricky to pull of. Thus, using DH significantly increase the cost and difficulty for the attacker. Since it forces him to be actively present during the hand shake, this also prevents large-scale passive snooping.
So to conclude, using DH would provide huge benefits in the sense of providing PFS. Also, it also provides some degree of protection of insider attacks, as long as the attacker stays passive.
So why was the 4WHS not designed to use DH?
Full disclosure: this will just be speculation on my part, since I do not know the arguments that went in to the design decisions of the IEEE 802.1i standard.
I guess that at the time WPA (or more correctly IEEE 802.11 RSNA) was designed, the value of PFS was probably not fully appreciated. In hindsight of the NSA revelations, it is of course easy for us to understand its importance now, but at that time it might not have been so clear. Thus, if you are not required to have PFS, and you already have a PSK available to your protocol, then there is a very simple reason why DH would not be used: efficiency. Symmetric primitives are much much more efficient than public-key primitives, hence if you can get away with only using that, the choice is obvious.
*Incidentally, the IEEE 802.11 standard actually do support a DH-based key-exchange built on a password-based AKE called Dragonfly. However, this variant is only used when the network is in ad-hoc mode.
- 2,865
- 19
- 23
It's the same reason why open WIFI isn't encrypted. It is feasible and we have the technology and means, but the problem lies in our inefficient nature as humans.
It makes perfect sense to use Diffie-Hellman/RSA, yet someone up there decided to standardize it in a non optimal way. The world is inefficient and standards move slower than mountains, numerous sub-optimal solutions are employed all across the world in all fields, not just cryptography.
In PSK, anyone who knows the pre-shared key and who has eavesdropped on the 4-way handshake gains un-encrypted access to your traffic. Using Diffie-Hellman/RSA cryptography would eliminate that weakness.
Also, achieving the WPA-Enterprise level of authentication is as simple as checking the wireless station's public key signature. That would prevent MITM. A simple example would be a small LED screen on a router, showing the public key signature. When the user connects to the hotspot for the first time, he has to confirm the public key signature is correct. If the signature changes in the future, the user gets a security warning. The LED screen was just an example, the key signature can be conveyed to the user in a variety of ways.
Some comments state that a Diffie-Hellman/RSA is redundant because you already have a key. That's a false statement because in this scenario Diffie-Hellman/RSA offers a clear advantage, thus it is NOT redundant.
WPA-Enterprise does solve the problem but it adds unnecessary complexity. Albert Einstein would love WPA with RSA/Diffie-Hellman.
"Keep it as simple as possible, but not simpler". -Albert Einstein
- 201
- 2
- 5
Using DH with public keys signed by the network wide PSK does not prevent station performing MITM attacks on each other. Further, if the PSK is weak a brute force attack on the signature applied to the public key can be a viable off line strategy. Subsequently to determining the PSK, the unauthorised 3rd party could then use the MITM attack to decrypt legitimate traffic. While this is technically challenging (from a radio perspective) cryptographically it appears to add little protection beyond perfect Forward Secrecy when compared to the existing PSK method.
Of course, stations should only do a single DH exchange on their 1st association to an AP but the open problem of the lack of authentication of WiFi management frames (e.g. spoofing failed association responses) and lack of user interaction at the AP (e.g. unlike Bluetooth pairing) opens an attack vector to induce DH exchanges on demand (as is currently possible with the 4-way handshake). In conclusion, DH with PSK signatures therefore raises the cost and complexity to perform an attack on the system but nowhere near as much is it does with other protocols that were more securely designed (e.g. IPsec).
Considering WPA-Enterprise offers (with the right EAP choice) per user keying and isolation, brute force resilience, and possibly even inter-session PFS. It offers all the same features discussed as advantageous with PSK-DH plus better access management (users can be de-authorised from the system without rekeying and restricted to certain login times or even to particular VLANS). I see why WPA-PSK was relegated to the a low cost/complexity consumer option. The few consumers that are privacy concerned (as opposed to just stopping their neighbours free loading) can obviously choose better PSKs and employ separate guest networks.
Probably, not the answer you wanted to hear but as "Hello World" alluded to PR and sales and profit margin is what drives a lot of these specs...
- 111
- 1
An update to this thread is appropriate now due to the WPA Krack vulnerability. Of course a four way handshake is not sufficient for the securing of a protocol such as WPA. Moving forward, any remediation to Krack will likely involve replacing the four way handshake with a DH. Again, the key exchange is a critical component in cryptography.
- 31
- 1
WPA2 or IEEE 802.11i-2004 came about in 2004. The fastest intel processor then was a Pentium 4.
Here are some benchmarks from around 2006: https://web.archive.org/web/20061201042628/https://www.cryptopp.com/benchmarks.html
DH 2048 Key Agreement 13.66 (milliseconds per operation)
For a two-party handshake, it would take twice as long. So 27 milliseconds. However this assumes you are willing to use a fifty watt processor for your router. Embedded processors at at least a tenth as powerful, so at least ten times as much time.
However, digital signal processors make extensive use of multipliers, so it could be argued that if you're doing networking, you can also do some public key cryptography.
- 721
- 1
- 5
- 18
Diffie Hellman is used in WPS in different context. A prime group and prime numbers are derived and public/private pair is derived/used subsequently for further derivation of KDK, EMSK etc.. Once the credential transfer is done safely the PTK is derived on either side and installed via four way handshake. In four way handshake there is no Diffie Hellman usage.