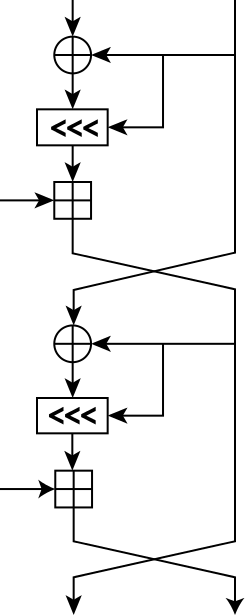
Most cryptographic primitives I've seen rotate by a constant. RC5 did something different though:
For a word size $w=2^n$, you can take the last $n$ bits of a value as a rotation amount. There's more sophisticated variants like that used in RC6.
To give these values a name: $A \lll B$.
Some good things:
- Rotations are fast
- Provides some diffusion
- Has some nonlinear properties
- Can be strong when combined with other operations
Some bad things:
- Parity of $A$ is preserved
- Differences in $A$ are preserved
- Only a few bits in $B$ are used
- Differences in $B$ may not have an effect (or have little effect)
- Less differences if $A$ is mostly (or all) 0s or 1s
- Less differences with alignment in $A$
- Multiple variable rotations are not proportionally better
There's probably some more subtle weaknesses that make it more susceptible to differential cryptanalysis, but nothing that totally breaks it I think, or RC5 would be unusable.