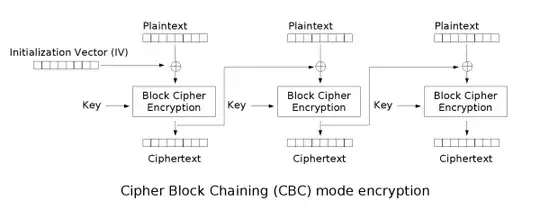
While reviewing a 'secure communication protocol' made by a colleague, I noticed a usage of AES-128 CBC that caught my eye. I think they are trying to implement a HMAC but have made some very questionable decisions.
The steps look like this:
- The IV is initialized to be the same as a user's (plaintext) password with just one byte changed.
- AES CBC takes the password, this IV, and a key as input, however the same key is used each time.
- The output of this encryption is then XORed with the original password, giving the user's password hash.
Now presuming I have the key and some hashed passwords, is it possible to obtain the original plaintext passwords, in order to prove to my colleague that this system is horribly broken?