You're essentially asking if SHA-3 can use a keyed hash instead of an HMAC.
The short answer is yes. But there's more to it than that.
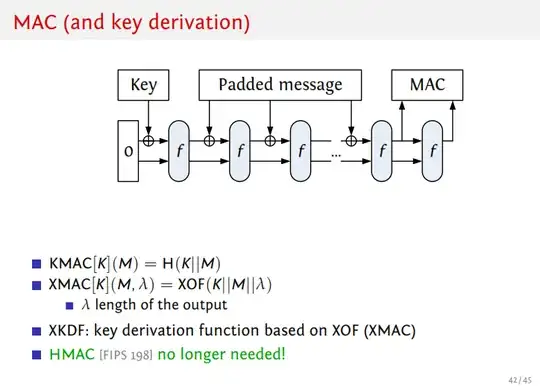
In the SHA-3 competition, two of the finalists (Keccak and Skein) were specifically designed to have a one-pass MAC as part of their design, and that's what the answer above is giving about Keccak. KMAC is Keccak's one-pass MAC. Skein also has a one-pass MAC. It's a fine answer — really, you ought to use KMAC rather than either a keyed hash or HMAC because KMAC has security proofs over a keyed hash and it's faster than HMAC. But that isn't the question you asked, you asked about keyed hashes.
But any of the five finalists are collision resistant enough that a keyed hash is likely to be as good as HMAC. In that word "likely" is presuming that they're as collision-resistant as presently thought. HMAC is a construction that protects against certain types of flaws in a hash function, but what that actually means is a huge discussion that you didn't ask about.
If you're going to do a keyed hash function, you should hash . I am presuming that your message has been canonicalized in whatever way you want. You want to hash the key before the message and the length of each field before the field because assuming hash flaws (like those that exist in Merkle-Damgård constructions), that puts the important things where they're less vulnerable to collision issues, and collisions are much harder.
The bottom line is that if you're going to use SHA-3, you should use KMAC. If you're using an HMAC, yes, you can drop-in-replace an older function with SHA-3 and that's even better. And yes, if you use a modern hash function like any of the SHA-3 finalists with a keyed hash, it can be as good as either.
— Jon (Skein co-author)