First of all, AES is like an alias for a winner of a contest that has started in 1997 and finishes in 2000 with the announcement of Rijndael's win. A nice document to learn AES is the link given by Richie Frame in the comments of this question.
Trying to do an small summary, there are two main families of symmetric ciphers and Rijndael is a member of the Substitution-Permutation Network (SPN). The other family is the Feistel Networks with DES as a highlighted member (the AES predecessor).
The main goal of a symmetric cypher is to provide enough confusion and diffusion (Shannon properties) and often this is provided by a set of rounds where different operations are applied on each of them. The key shall be applied in those rounds, and in the case of Rijndael is not the key itself, but parts of a Key Derivation Function.
Long a go I've wrote something, and perhaps the image I've made could help you to understand the iterative process of the KDF in Rijndael. It had a mistake and I'm placing here a fixed version of the image. That is for 128 bit keys, but it's not hard to imagine how different it is with the other key sizes.
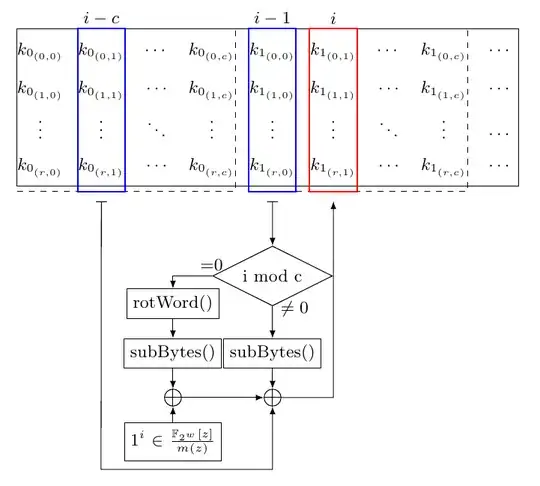
Rijndael have some good characteristics like efficiency in software and in hardware, specially because in the lowest level all the operations are bit xors (but this has been already pointed in the comments). Perhaps one cons would be the complexity to protect against side channel attacks.
