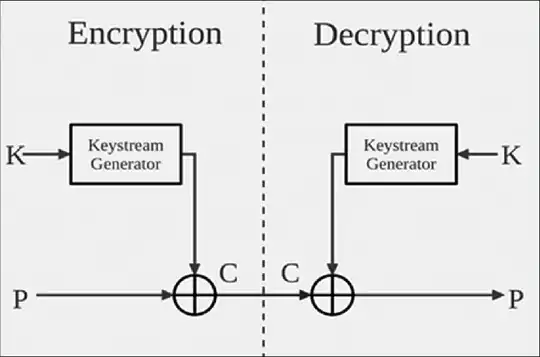
Edit: For any additive group operation, including addition modulo $k$ if the added keystream symbols $z_t$ are uniformly distributed, which means
$$
Pr(z_t=a)=1/k, \quad \forall a \in
\{0,\ldots, k-1\}
$$
then the ciphertext symbols $c_t=x_t+z_t \pmod k$ are themselves uniformly distributed, $x_k$ being the plaintext symbol. You can show this in exactly the same manner as in the new answer by @user93353. Essentially addition of symbols corresponds to convolution of the probability distributions of $z_t$ and $x_t$ to get the probability distribution of $c_t$.
The idea of using addition is older than modern ciphers. In classical alphabetic ciphers, addition modulo $k$ over a finite alphabet of size $k$ will work. Note that XOR is a special case of this where addition is modulo 2.
Addition modulo $k$ just means that you add $a,b \in \{0,1,\ldots,k-1\}$ by taking the remainder after division by $k,$ if necessary; this is sometimes informally referred to as clock addition: If the time is 10 am, 4 hours later the time is
$10+4 = 14 \pmod{12} \equiv 2$ hence you obtain 2 pm.
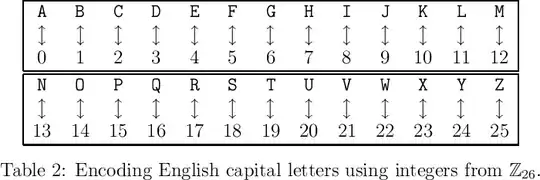
Consider the alphabet $\{A,B,\ldots,Z\}$ modelled by $\mathbb{Z}_{26}$ the integers modulo 26 under addition where
we have the encoding
$$
A\leftrightarrow 0, B\leftrightarrow 1,\ldots,Z\leftrightarrow 25.
$$
or pictorially
If you have the plaintext ATTACK it is represented by the sequence $$0,19,19,0,2,10$$
and if you additively apply the key SECRET represented by the sequence
$$18,4,2,17,4,19$$
you obtain the ciphertext
$$
0+18,19+4,19+2,0+17,2+4,10+19=18,23,21,17,6,29
$$
which after applying the modulo 26 reduction becomes
$$
18,23,21,17,6,3
$$
giving the ciphertext SXVRGC.