Frequency analysis is the study of letters or groups of letters contained in a ciphertext in an attempt to partially reveal the message.
Frequency analysis is the study of letters or groups of letters contained in a ciphertext in an attempt to partially reveal the message.
The English language (as well as most other languages) have certain letters and groups of letters appear in varying frequencies. The following chart shows the frequency distribution of letters in the English alphabet:
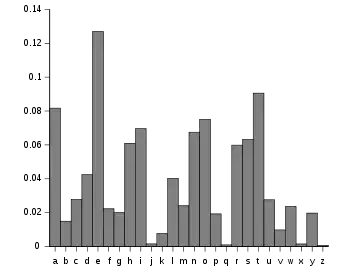
image source: Wikipedia
As you can see, the letter e is the most common, while j,q and x are very uncommon.
If the encryption method does not effectively mask these frequencies, it is possible to statistically determine parts of the plaintext from looking at the ciphertext alone… based on knowing the usual frequencies of letters in English communication.
Many classical ciphers are vulnerable to frequency analysis.