Is AES GCM without GMAC vulnerable against bit-flip attacks? Let's assume the plaintext is known for some reason (e.g. it can be guessed). In my opinion, I can flip bits in the ciphered blocks and can so generate a plaintext, which is flipped at the same position. So it would be easy to change 0x01 to 0x00 in the plaintext, even when I don't know the key or Initialization vector.
1 Answers
As an Authenticated Encryption with Associated Data, AES-GCM internally uses CTR mode and GCM adds authentication and integrity. Without GCM one can have only Ind-CPA security.
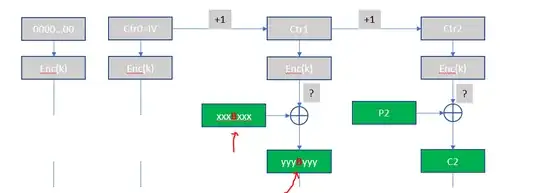
CTR in AES-GCM starts IV incremented ($inc_{32}(J_0)$ in NIST format and if IV size is not 96-bit then the IV is processed). The initial $J_0$ is used in the authentication tag calculation.
The rest is the usual CTR mode. If one knows the message, they can change the message into whatever message they want. Just x-or (the bit-flip attack) the necessary bits.
Consider the encryption. One has no control of the output stream. On the other hand, if the ciphertext is modified, only the plaintext is changed. Or see in the equation;
$$C_i = O_i \oplus P_i$$ The output stream $O_i$ is fixed by the block cipher encryption therefore changing the $C_i$ modifies the $P_i$.
This is, however, is not a known-plaintext attack! In a known-plaintext attack, one has known-plaintext pairs and tries to determine the key. CTR mode is secure against KPA attacks and actually, that is a lesser attack than Ind-CPA.
- 49,797
- 12
- 123
- 211