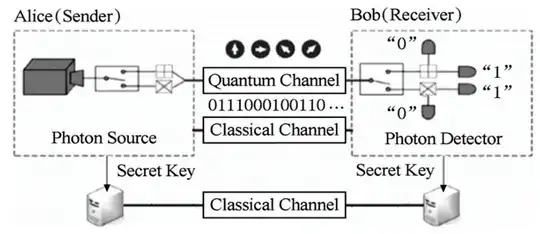
I am currently implementing some QKD protocols using Qiskit and I came up with the following question: After the protocol is finished, a true random password is generated using 0s and 1s, however, and here my question, do these passwords need to be converted to another base? Maybe hexadecimal? Or are they used as they are?
When I mean by used is to using them, for instance, as a key for the one time pad.