I'm playing with Contiki (O.S. for constrained devices such as sensors and micro-controllers) and particularly with the AES encryption in software (the one available in Contiki source code).
I'm trying to complete the code by adding the decryption operation, but I'm confused with the inverse MixColumns operation. They are using the paper Lightweight MixColumns for it (because it can reduce the number of XOR gates in hardware). On the page 257 they state that:
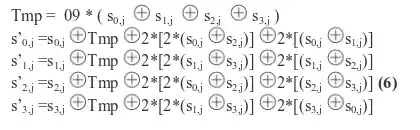
QUESTION: Would be correct to say that the first line is equivalent to the following code? (inspired by a similar question) :
//buf1 * 9 = ((( buf1 x2) x2) x2)+ buf1
buf1 = state[buf4] ^ state[buf4 + 1] ^ state[buf4 + 2] ^ state[buf4 + 3];
buf2 = galois_mul2(buf1);
buf2 = galois_mul2(buf2);
buf1 = galois_mul2(buf2) ^ buf1;
Currently, my decryption function is not working, but not sure if it's because I'm screwing up in another part of the code or at this point.