TRNGs are better than cryptographic algorithms that generate pseudo-random numbers (PRNGs) because these algorithms are more energy intensive than TRNGs
Random number generation in IoT devices is necessary and challenging, with many proposed solutions. However, any modern computing system (including IoT devices) will have some kind of TRNG if they need random numbers. Albeit, the minimum entropy (also discussed here) that can be extracted from each type of random event, in any set amount of time, may vary widely between each. TRNGs on their own are typically not suitable for many cryptographic uses, because the trueness(0)(1) of their randomness does not imply the non-bias uniformity of their outputs. This non-uniformity may be of particular issue when translating from a measurement domain (for instance $\mathbb R$) to the domain of requested randomness (usually, but not limited to, $\subset \mathbb N_0$).
The approach is almost always to use both TRNGs, to sample randomness, and PRNGs, to mix new randomness with stored randomness into unique, unguessable, uniform(2) and statistically independent(3) outputs. In such a system, which is well-designed and implemented, having access to any number of outputs should not help in guessing past or future outputs. If a system is only using a TRNG with no kind of PRNG, I would be highly suspect, even if the TRNG is shown to be less energy intensive.
Would there be any benefit to using TRNGs in those? If we don't use TRNGs in them, why is that?
We do, and they are very useful, as explained above.
And if we do, which ones are the gold standard?
There are many great sources of true randomness. But any one of them may fail, or otherwise be insufficient due to speed of generation, quality or unavailability (malicious or incidental). The standard(4) is to use collections of TRNGs together to minimize the chance of catastrophic failure.
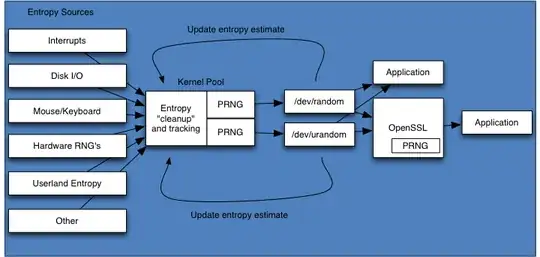
Fig. 1 | Illustration of a typical entropy life-cycle management system.
It's generally accepted that the faster, more uniformly distributed, more entropic and more efficient, the better. But the point of using PRNGs and TRNGs together, perhaps to create a CSPRNG, is that: Once enough initial randomness has been acquired, speed, uniformity and entropy can be gained by continuously seeding the pools with even rather low-quality TRNGs, and then extracting outputs using an efficient PRNG, such as a light-weight symmetric cipher or hash function.
