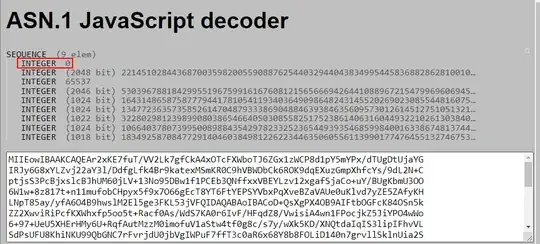
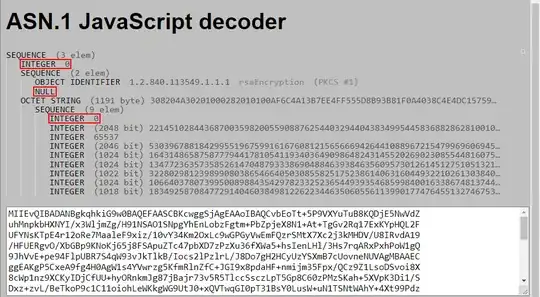
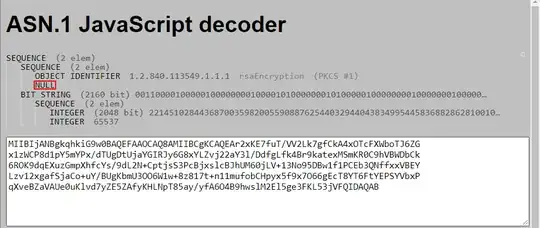
Will the "version" fields (i.e. INTEGER 0) always be zero for the specified structure?
As long as one is dealing with standard "biprime" RSA, that is the kind with the public modulus having two distinct primes $p$ and $q$, it's a safe bet one won't meet version other than 0 in a PKCS#1 RSAPrivateKey, including in such structure embedded in a PKCS#8 structure. version 1 is specifically for multiprime RSA, where the modulus can have three or more (distinct) prime factors. There's nothing to prevent using version 1 for biprime RSA, but that's definitely not customary.
From PKCS#1 v2.2; see especially CONSTRAINED BY…
RSAPublicKey ::= SEQUENCE {
modulus INTEGER, -- n
publicExponent INTEGER -- e
}
--
-- Representation of RSA private key with information for the CRT algorithm.
RSAPrivateKey ::= SEQUENCE {
version Version,
modulus INTEGER, -- n
publicExponent INTEGER, -- e
privateExponent INTEGER, -- d
prime1 INTEGER, -- p
prime2 INTEGER, -- q
exponent1 INTEGER, -- d mod (p-1)
exponent2 INTEGER, -- d mod (q-1)
coefficient INTEGER, -- (inverse of q) mod p
otherPrimeInfos OtherPrimeInfos OPTIONAL
}
Version ::= INTEGER { two-prime(0), multi(1) }
(CONSTRAINED BY {-- version must be multi if otherPrimeInfos present --})
OtherPrimeInfos ::= SEQUENCE SIZE(1..MAX) OF OtherPrimeInfo
OtherPrimeInfo ::= SEQUENCE {
prime INTEGER, -- ri
exponent INTEGER, -- di
coefficient INTEGER -- ti
}
The version field of an extended PKCS#8 structure has been assigned the value 1 in a new RFC, see dave_thompson_085's comment, though we have no report of seeing other than 0 in the wild (still, I lost my bet that a whole new structure would be created instead should an extension become desirable).
I'll refrain from commenting the NULL that are following the OIDs, for I fail to track their nature.
Note: when parsing or generating ASN.1 in crypto, there are two choices:
- Building a small ad-hoc parser/generator for an ASN.1 DER structure at hand; in this case it's essential to stop parsing as soon as something unexpected is met, or we start to parse outside the input.
- Using a full-fledged library. This tends to be a huge and complex piece of software, perhaps with bugs, and even more probably with bugs in how a beginner uses it. However, past a certain degree of complexity, including parsing X.509 certificates of unspecified origin or anything BER, PER or more complex, that's perhaps a necessity.