[Moderator note: this question now lives there]
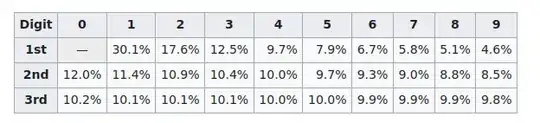
So, I'm preparing a talk about the well known fact that humans are bad at the task of generating uniformly random sequences of numbers when asked to do so, which is a huge flaw for simple cryptographic systems.
I would like to spice the talk a bit by present some real cases where perhaps some tax fraud or bad science was revealed by a simple frequency analysis of the compromised data. For example a case were a scientist might have displaced some data points to better fit a specific conclusion and that it was discovered by analyzing the end digits of the values he manipulated. Or perhaps some person that changes a few small numbers here and there while working for a bank to get some money flowing to his account and then was discovered by another simple analysis.
In short, I would like to know easy to explain examples of people been caught in some fraud because they though that they were able to emulate random numbers by themselves.
I don't know if this is the correct place to ask for this kind of question but Physics and Law stacks seemed less related.